Master-Slave Transactional Incremental Replication
Version 1.0.0 GotDotNet community for collaboration on this pattern Complete List of patterns & practices
Context You are about to design the handling of transmissions on a replication link. Your requirements are:
You have decided to achieve this by replicating the changes on a transactional level. Thus, you must retrieve transactional information from the source by either by accessing the transaction log of the database system or by preparing the source database as described in the Capture Transactional Detailspattern . Since the granularity of a transmission is a transaction, both source and target have to be database management systems (DBMSs), which we will describe in relational DBMS (RDBMS) terms.
Problem How do you design a replication link to support the transmission of transactional changes, and to replay them on the target while meeting all integrity requirements? Forces Any of the following compelling forces justify using the solution described in this pattern:
The following enabling forces facilitate the adoption of the solution, and their absence may hinder such a move:
Solution The solution is to acquire the information about committed transactions from the source and to replay the transactions in the correct sequence when they are written to the target.
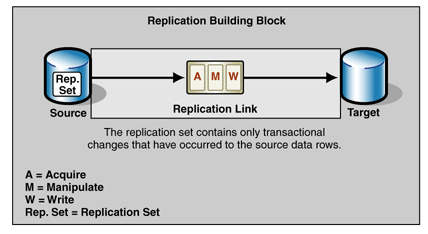
Figure 1 shows the replication building block for this type of replication.
Figure 1: Replication building block for Master-Slave Transactional Incremental Replication
Depending on the features of the RDBMS and on the requirements of the replication link, the transactional information can be acquired either from the logging system of the source or from additional schema objects on the source. In both cases, the effects of the transaction are acquired as a collection of operations on the rows being updated by the transaction. The transmission to the target results in the corresponding rows being updated by transactions of the same size and in the correct sequence (according to their completion time at the source).
The detailed description of this pattern is separated into: Background
Before starting to describe the design of a transactional replication link, here are two considerations of more general nature: Transaction Order for Replay
When replaying the transactions on the target, you do not have to mirror the database connection environment on the target to achieve data integrity. As concurrent transactions are isolated from each other, you can execute the transactions on the target sequentially instead. Thus, you can use a single database connection to replay all transactions of the current transmission. However, you must execute the individual transactions in the correct sequence, which is given by the time of their completion on the source.
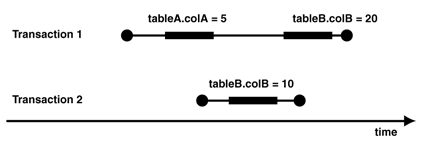
The following example shows why the transactions must be ordered by their completion time, not their start time.
Two tables are written by two concurrent transactions. Figure 2 shows how both transactions are running in parallel.
Figure 2: Two concurrent transactions
Transaction 1 starts first and updates tableA. Then Transaction 2 starts, updates tableB, and completes with a commit. Finally, Transaction 1 also updates tableB. After both transactions, colB of tableB has a value of 20.
If the ordering were done on the transaction start time, the update of Transaction 2 would be the last one. Thus, colB of tableB would have a value of 10 at the end, instead of 20. However, if the ordering is done on the end time of each transaction, colB of tableB has a value of 20 at the end, which is the correct value.
If Transaction 1 had written tableB before Transaction 2 (for example, instead of tableA), then Transaction 2 would have been blocked until the end of Transaction 1. Transaction 2 would have been executed after Transaction 1, and colB of tableB would have a value of 10. Here again the transactions have to be ordered on their completion, which produces the correct result.
A sufficiently precise timestamp is needed to distinguish the completion time of any two transactions and thereby correctly order the transactions. Handling Triggers, If the Write Uses Standard SQL
Triggers are schema objects that perform additional operations on behalf of an initial operation. Triggered operations are also part of the initiating transaction and are logged in the same way as any other operation.
There is an issue around how the RDBMS behaves when logged changes get applied to the target database. If you can apply the log information to the target without ever triggering a secondary operation, then you are fine. But if a trigger could be fired by applying a log record, then you have to be concerned.
This applies to either triggers that match source ones, or totally different triggers at the target.
For example, a source table has a trigger that is fired on every UPDATE. This would INSERT the old state of the row into a history table. There is a similar trigger on the target table. An UPDATE of the row in the source log is recorded, and the triggered INSERT into the history table is also recorded as part of the transaction. When executing this transaction on the target, the UPDATE of the table is performed first. This fires the trigger on the target, which causes an entry into the history table. But the source also recorded an INSERT into the history table. When replaying the next operation, a second INSERT into the history table is performed. Thus, the history table would have two new entries instead of one.
Hence, if you don't take special precaution around the handling of triggers, you might perform more operations on the target than you performed on the source.
To solve the problem, you must eliminate the effect of the trigger on the target during transmissions. To achieve this, the replication link should connect to the target database with a dedicated user or a dedicated role that is only used for transmissions, but not by any other applications. Additionally, the trigger has to be defined in a manner (depending on the SQL dialect of the RDBMS) that does not perform any operations if the database connection uses this special user or role. Prerequisites
This pattern depends on two features that the DBMS must provide and on a prerequisite for the data model: Elements of the Replication Building Block
The following paragraphs describe the elements of the replication building block for this type of replication. Source
The source contains the replication set, which is a log of all changes that you want to acquire. Acquire
The steps of Acquire are:
1.Connect to the source.
2.Find the transaction pending for transmission to the target that has the oldest completion timestamp.
3.Find the first operation of this transaction.
4.Pass the Transaction Identifier, the table name, the type of operation (INSERT, UPDATE, or DELETE) and the names and values of the columns to Manipulate.
5.Continue with step 4 until all operations for the current transaction are read.
6.Delete the record of the transmitted transaction, unless it is needed for other replication links.
7.Continue with step 2 until all transactions are read. Manipulate
This service performs the following steps:
1.Get the first row from Acquire.
2.If the table needs some manipulation, perform the appropriate action, such as converting data types, and combining or splitting fields of the row.
3.Pass the Transaction Identifier, the table name, the type of operation (INSERT, UPDATE, or DELETE) and the names and values of the columns to the Write service.
4.Get the next row from Acquire and continue with step 2 until all rows are processed. Write
The Write service performs the following steps:
1.Get the first row from Manipulate.
2.If the Transaction Identifier differs from the Transaction Identifier of the previously handled row, COMMIT the transaction.
3.Depending on the remaining attributes, build a SQL statement that INSERTs, UPDATEs, or DELETEs a single row in the target.
4.Get the next row from the Manipulate service and continue with step 2 until all rows are processed. Target
The target is the database where the transactions are replayed. You must ensure that no triggered operations are executed, as described above. Example The Implementing Master-Slave Transactional Incremental Replication Using SQL Server pattern presents an implementation of the design pattern by the means provided with Microsoft SQL Server. Resulting Context The use of this pattern inherits the benefits and liabilities from Master-Slave Replication and has the following additional benefit and liability: Benefit
Liability
Security Considerations The database connection used to replay the transactions on the target must have sufficient access rights to INSERT, UPDATE, or DELETE in all tables belonging to the replication set. In addition, the Acquire database connection account needs to have SELECT or READ privileges on the source transaction objects. It is recommended that you create a dedicated user in the target database with appropriate privileges and use this user for all transmissions. In general, this user will not be used for any other purposes. Defining such a user allows you to tailor the privileges to the specific needs of Acquire or Write. Operational Considerations Before implementing Master-Slave Transactional Incremental Replication, the following are considerations to achieve smooth running operations: Variants After introducing the solution for transmitting the changes of a replication set from the source to the target, two variants show possible enhancements. The first variant shows a way to obtain a higher robustness of the replication. The second one sketches the implementation of a change history. Higher Robustness
When writing the transactions to the target, you might consider converting INSERTs into UPDATEs or vice versa. Thus, if an INSERT raises a duplicate key error, you perform an UPDATE instead; and if the number of rows being hit by an UPDATE is zero, you perform an INSERT instead. This is sometimes referred to as an UPSERT.
Although such error handling is not necessary as long as the content of the target corresponds exactly to the state of the source before the transaction, it offers a higher degree of robustness. If the content of the target had been changed, for example, by an erroneous action of an operation or administrator, the normal execution of the transaction would fail; however, such an error handling will again align the contents of the source and the target. Implementing a Change History
Instead of updating changed rows, they can be appended by adding a version number. Therefore, the previous version of the target row will be kept to retain a change history at the target. For example, this information can be used to trace a stock's performance record. Additional Prerequisites
Some preparations have to be made for this variant to work. Operational Considerations
Because rows will not be updated but inserted, the target database grows faster than the source database. Therefore, you must provide an appropriate amount of free disk space at the target site. Related Patterns For more information, see the following related patterns: Patterns That May Have Led You Here
Patterns That You Can Use Next
Other Patterns of Interest
|